Sticky Postings
All 242 fabric | rblg updated tags | #fabric|ch #wandering #reading
By fabric | ch
-----
As we continue to lack a decent search engine on this blog and as we don't use a "tag cloud" ... This post could help navigate through the updated content on | rblg (as of 09.2023), via all its tags!
FIND BELOW ALL THE TAGS THAT CAN BE USED TO NAVIGATE IN THE CONTENTS OF | RBLG BLOG:
(to be seen just below if you're navigating on the blog's html pages or here for rss readers)
--
Note that we had to hit the "pause" button on our reblogging activities a while ago (mainly because we ran out of time, but also because we received complaints from a major image stock company about some images that were displayed on | rblg, an activity that we felt was still "fair use" - we've never made any money or advertised on this site).
Nevertheless, we continue to publish from time to time information on the activities of fabric | ch, or content directly related to its work (documentation).
Wednesday, March 23. 2016
The Birth And Death Of Privacy: 3,000 Years of History Told Through 46 Images | #privacy #transparency #history
Note: to put things in perspective, especially in the private-public data debate, it is interesting to start digg into the history of privacy, or how, where and when it possibly came from... So as how, where and when it will possibly vanish...
The following article was found on Medium, written by journalist Greg Ferenstein. It has some flaws (or rather some quick shortcuts due to its format) and seems driven by the statement that the natural state of human beings is "transparency/no privacy", but it also doesn't pretend to be a scientific final story about privacy. It is rather instead a point of view and a relatively brief introduction by a writer, considering the large period adressed (to start digg in then). It is not a detailed paper by an historian specialized into this topic.
The article should be taken with a bit of critical distance therefore. Especially, to my reader's point of view, there are missing arguments regarding the fact that "privacy" is obviously not mainly "physical privacy" (walls, curtains, etc.), or not anymore for a long time. It certainly started as physical privacy -- as the author demonstrates it well -- but at a critcal point, this gained privacy, this evolution from a state of "no privacy" helped guarantee a certain freedom of thinking that became therefore highly related to the foundation of our "democratic" political system, to the "enlightenment" period as well.
And this is the main element regarding this question according to me. Loosing one could also clearly mean loosing the other... (if it's not already lost... a subject that could be debated as well, not to speculate further to know if a different system could emerge from this nor not, maybe even an "egalitarian" one).
Also, to state as a conclusion (last 7 lines) that our "natural state" is to be "transparent" (state of no privacy) and that the actual move toward "transparency" is just a manner to go "naturally" back to what it always was is a bit intellectually lazy: the current "transparency" that is pushed mainly by big corporations and also by States for security reasons --as stated, "law enforcements" of many sorts-- is not the old "passive" transparency but a highly "dynamic", computed, processed, and often merchandised one.
It has nothing to do with the old "all the family lives naked with their nurturing animals in the same room" sort of argument then... It is a different system, not democratc anymore but a mix of ultra liberalism and monitored surveillance. Not a funny thing at all...
So, all in all, the arguments in the article remain very interesting, related to many contemporary issues and there are several useful resources as well in there. But you should definitely keep your brain "switch on" while reading it!
Via Medium
-----

Jean-Leon Gerome, The Large Pool Of Bursa
2-Minute Summary ...
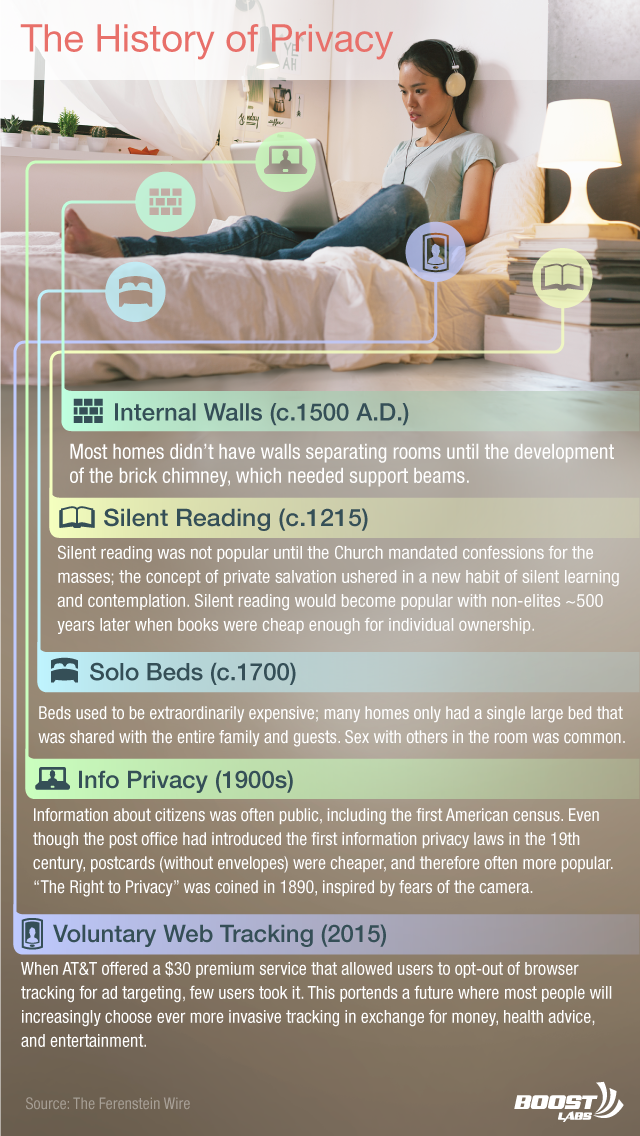
- Privacy, as we understand it, is only about 150 years old.
- Humans do have an instinctual desire for privacy. However, for 3,000 years, cultures have nearly always prioritized convenience and wealth over privacy.
- Section II will show how cutting edge health technology will force people to choose between an early, costly death and a world without any semblance of privacy. Given historical trends, the most likely outcome is that we will forgo privacy and return to our traditional, transparent existence.
*This post is part of an online book about Silicon Valley’s Political endgame. See all available chapters here.
SECTION I:
How privacy was invented slowly over 3,000 years
“Privacy may actually be an anomaly” ~ Vinton Cerf, Co-creator of the military’s early Internet prototype and Google executive.
Cerf suffered a torrent of criticism in the media for suggesting that privacy is unnatural. Though he was simply opining on what he believed was an under-the-radar gathering at the Federal Trade Commission in 2013, historically speaking, Cerf is right.
Privacy, as it is conventionally understood, is only about 150 years old. Most humans living throughout history had little concept of privacy in their tiny communities. Sex, breastfeeding, and bathing were shamelessly performed in front of friends and family.
The lesson from 3,000 years of history is that privacy has almost always been a back-burner priority. Humans invariably choose money, prestige or convenience when it has conflicted with a desire for solitude.
Tribal Life (~200,000 B.C. to 6,000 B.C)

Flickr user Rod Waddington
"Because hunter-gatherer children sleep with their parents, either in the same bed or in the same hut, there is no privacy. Children see their parents having sex. In the Trobriand Islands, Malinowski was told that parents took no special precautions to prevent their children from watching them having sex: they just scolded the child and told it to cover its head with a mat" - UCLA Anthropologist, Jared Diamond
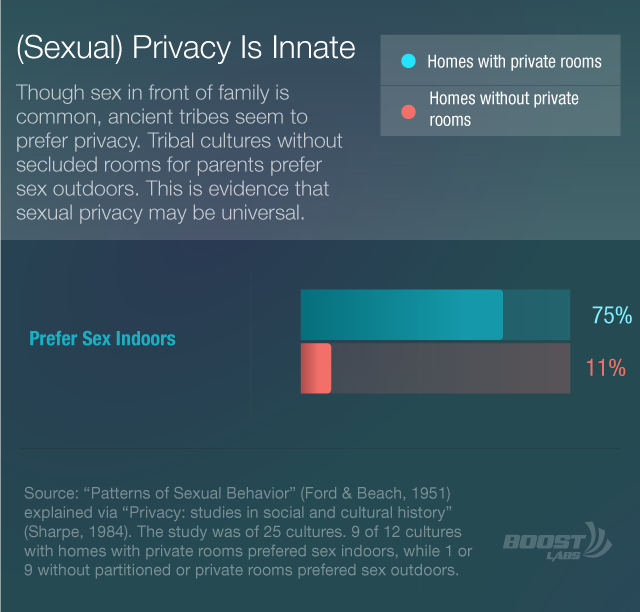
While extremely rare in tribal societies, privacy may, in fact, be instinctive. Evidence from tribal societies suggests that humans prefer to make love in solitude (In 9 of 12 societies where homes have separate bedrooms for parents, people prefer to have sex indoors. In those cultures without homes with separate rooms, sex is more often preferred outdoors).
However, in practice, the need for survival often eclipses the desire for privacy. For instance, among the modern North American Utku’s, a desire for solitude can seem profoundly rude:

Inuit family. Source: Wikipedia Ansgar Walk
...
"It dawned on me how forlorn I would be in the wildness if they forsook me. Far, far better to suffer loss of privacy” - Anthropologist Jean Briggs, on being ostracized by her host Utku family, after daring to explore the wilderness alone for a day.
...
The big question: if privacy isn’t the norm, where did it start? Let’s start from the first cities:
Ancient Cities (6th Century B.C. — 4th Century AD)

Image: Roman citizens engaged in conversation in a public restroom. Credit: A Day In The Life Of Ancient Rome
Like their tribal ancestors, the Greeks displayed some preference for privacy. And, unlike their primitive ancestors, the Greeks had the means to do something about it. University of Leicester’ Samantha Burke found that the Greeks used their sophisticated understanding of geometry to create housing with the mathematically minimum exposure to public view while maximizing available light.

Sightline analysis of maximum viewable space from the street. Burke (2000)
“For where men conceal their ways from one another in darkness rather than light, there no man will ever rightly gain either his due honour or office or the justice that is befitting” - Socrates
Athenian philosophy proved far more popular than their architecture. In Greece’s far less egalitarian successor, Rome, the landed gentry built their homes with wide open gardens. Turning one’s house into a public museum was an ostentatious display of wealth. Though, the rich seemed self-aware of their unfortunate trade-off:

“Great fortune has this characteristic, that it allows nothing to be concealed, nothing hidden; it opens up the homes of princes, and not only that but their bedrooms and intimate retreats, and it opens up and exposes to talk all the arcane secrets” ~ Pliny the Elder, ‘The Natural History’, circa 77 A.D
The majority of Romans lived in crowded apartments, with walls thin enough to hear every noise. “Think of Ancient Rome as a giant campground,” writes Angela Alberto in A Day in the life of Ancient Rome.
...
https://www.youtube.com/watch?v=HhwXipv3tRU
...
And, thanks to the Rome’s embrace of public sex, there was less of a motivation to make it taboo—especially considering the benefits.

Sex art, Pompeii
“Baths, drink and sex corrupt our bodies, but baths, drink and sex make life worth living” - graffiti — Roman bath
Early Middle Ages (4th century AD-1,200 AD): Privacy As Isolation

Early Christian saints pioneered the modern concept of privacy: seclusion. The Christian Bible popularized the idea that morality was not just the outcome of an evil deed, but the intent to cause harm; this novel coupling of intent and morality led the most devout followers (monks) to remove themselves from society and focus obsessively on battling their inner demons free from the distractions of civilization.
“Just as fish die if they stay too long out of water, so the monks who loiter outside their cells or pass their time with men of the world lose the intensity of inner peace. So like a fish going towards the sea, we must hurry to reach our cell, for fear that if we delay outside we will lost our interior watchfulness” - St Antony of Egypt
It is rumored that on the island monastery of Nitria, a monk died and was found 4 days later. Monks meditated in isolation in stone cubicles, known as “Beehive” huts.

Even before the collapse of ancient Rome in 4th century A.D., humanity was mostly a rural species
A stylized blueprint of the Lord Of The Rings-looking shire longhouses, which were popular for 1000 years, shows animals and humans sleeping under the same room—because, there was only one room.
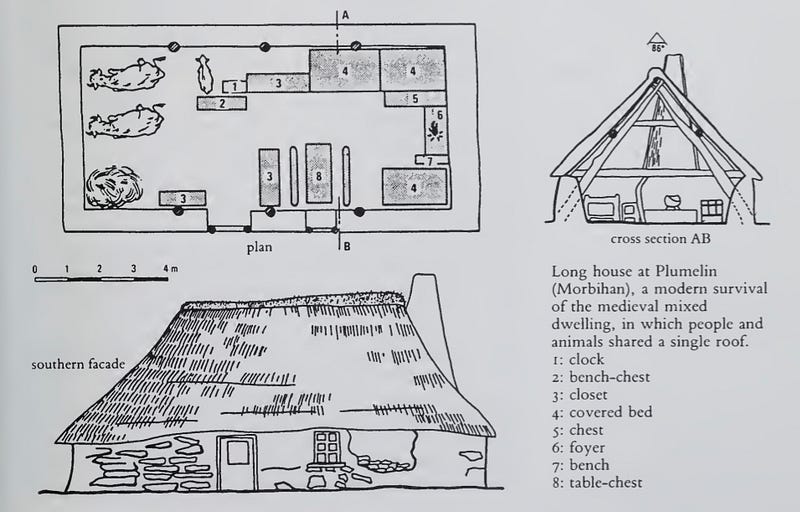
Photo credit: Georges Duby, A History Of Private Life: Revelations of the Medieval World
“There was no classical or medieval latin word equivalent to ‘privacy’. privatio meant ‘a taking away’” - Georges Duby, author, ‘A History Of Private Life: Revelations of the Medieval World’
Late Medieval/Early Renaissance (1300–1600) — The Foundation Of Privacy Is Built

“Privacy — the ultimate achievement of the renaissance” - Historian Peter Smith
In 1215, the influential Fourth Council Of Lateran (the “Great Council”) declared that confessions should be mandatory for the masses. This mighty stroke of Catholic power instantly extended the concept of internal morality to much of Europe.
“The apparatus of moral governance was shifted inward, to a private space that no longer had anything to do with the community,” explained religious author, Peter Loy. Solitude had a powerful ally.

...
Fortunately for the church, some new technology would make quiet contemplation much less expensive: Guttenberg’s printing press.

Thanks to the printing presses invention after the Great Counsel’s decree, personal reading supercharged European individualism. Poets, artists, and theologians were encouraged in their pursuits of “abandoning the world in order to turn one’s heart with greater intensity toward God,” so recommended the influential canon of The Brethren of the Common Life.

To be sure, up until the 18th century, public readings were still commonplace, a tradition that extended until universal book ownership. Quiet study was an elite luxury for many centuries.

Citizens enjoy a public reading.
...
The Architecture of privacy
Individual beds are a modern invention. As one of the most expensive items in the home, a single large bed became a place for social gatherings, where guests were invited to sleep with the entire family and some servants.

People gather around a large bed.
...
But, the uncleanness of urbanized life quickly caught up with the Europeans, when infectious diseases wiped out large swaths of newly crowded cities. The Black Death, alone, killed over 100 million people.
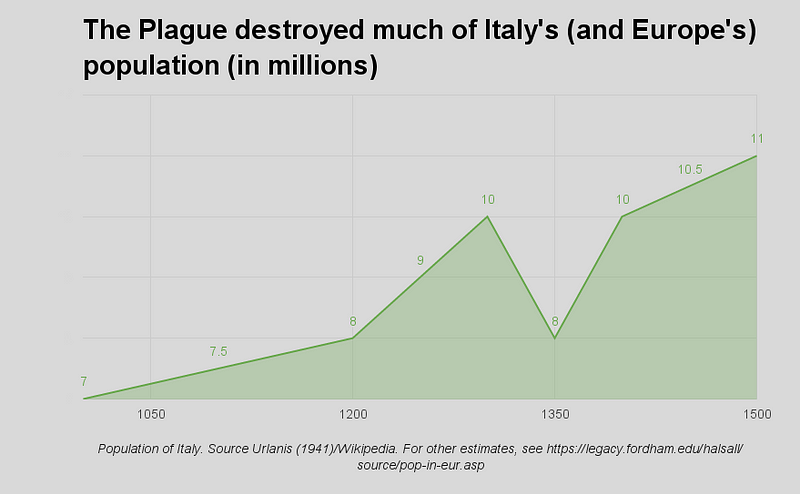
This profoundly changed hygiene attitudes, especially in hospitals, where it was once common for patients to sleep as close together as houseguests were accustomed to.

"Little children, both girls and boys, together in dangerous beds, upon which other patients died of contagious diseases, because there is no order and no private bed for the children, [who must] sleep six, eight, nine, ten, and twelve to a bed, at both head and foot" - notes of a nurse (circa 1500), lamenting the lack of modern medical procedures.
Though, just because individual beds in hospitals were coming into vogue, it did not mean that sex was any more private. Witnessing the consummation of marriage was common for both spiritual and logistical reasons:

“Newlyweds climbed into bed before the eyes of family and friends and the next day exhibit the sheets as proof that the marriage had been consummated” - Georges Duby, Editor, "A History of Private Life"
...
Few people demanded privacy while they slept because even separate beds wouldn’t have afforded them the luxury. Most homes only had one room. Architectural historians trace the origins of internal walls to the more basic human desire to be warm.
Below, in the video, is a Hollywood re-enactment of couples sleeping around the burning embers of a central fire pit, from the film, Beowulf. It’s a solid illustration of the grand hall open architecture that was pervasive before the popularization of internal walls circa 1,400 A.D.
...
https://www.youtube.com/watch?v=UT4gELLPPzs > Couples sleep around the warmth of a fire (clip from Beowulf)
...
“Firstly, I propose that there be a room common to all in the middle, and at its centre there shall be a fire, so that many more people can get round it and everyone can see the others faces when engaging in their amusements and storytelling” - 15th century Italian Architect, Sebastian Serlio.
...
To disperse heat more efficiently without choking houseguests to death, fire-resistant chimney-like structures were built around central fire pits to reroute smoke outside. Below is an image of a “transitional” house during the 16th century period when back-to-back fireplaces broke up the traditional open hall architecture.
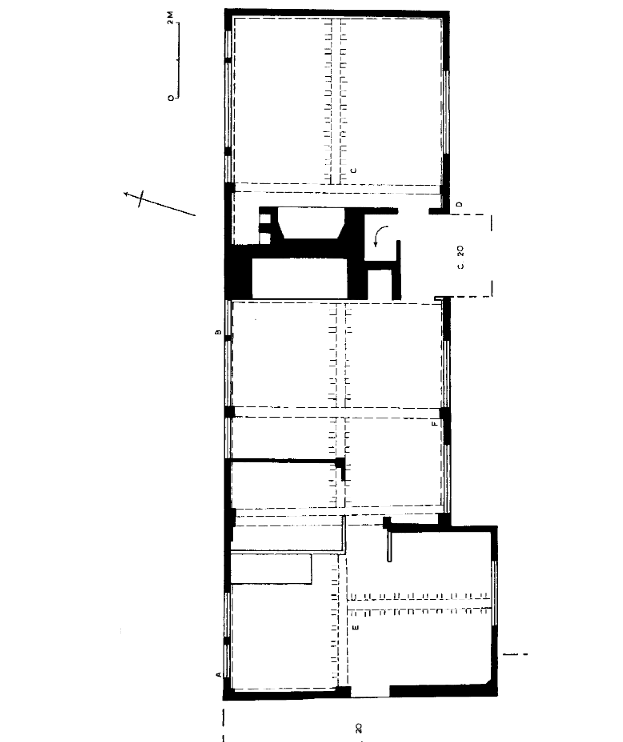
Source: Housing Culture: Traditional Architecture In An English Landscape (p. 78).
“A profound change in the very blueprint of the living space” - historian Sarti Raffaella, on the introduction of the chimney.
Pre-industrial revolution (1600–1840) — The home becomes private, which isn’t very private

The first recorded daily diary was composed by Lady Margaret Hoby, who lived just passed the 16th century. On February 4th, 1600, she writes that she retired “to my Closit, wher I praid and Writt some thinge for mine owne priuat Conscience’s”.

Cardinal Albrecht of Brandenburg in his study
By the renaissance, it was quite common for at least the wealthy to shelter themselves away in the home. Yet, even for those who could afford separate spaces, it was more logistically convenient to live in close quarters with servants and family.
“Having served in the capacity of manservant to his Excellency Marquis Francesco Albergati for the period of about eleven years, that I can say and give account that on three or four occasions I saw the said marquis getting out of bed with a perfect erection of the male organ” - 1751, Servant of Albergati Capacelli, testifying in court that his master did not suffer from incontinence, thus rebutting his wife’s legal suit for annulment.
...
Law
...
It was just prior to the industrial revolution that citizens, for the first time, demanded that the law begin to keep pace with the evolving need for secret activities.
In this early handwritten note on August 20th, 1770, revolutionist and future President of the United States, John Adams, voiced his support for the concept of privacy.
“I am under no moral or other Obligation…to publish to the World how much my Expences or my Incomes amount to yearly.”

Despite some high-profile opposition, the first American Census was posted publicly, for logistics reasons, more than anything else. Transparency was the best way to ensure every citizen could inspect it for accuracy.
Privacy-conscious citizen did find more traction with what would become perhaps America’s first privacy law, the 1710 Post Office Act, which banned sorting through the mail by postal employees.

“I’ll say no more on this head, but When I have the Pleasure to See you again, shall Inform you of many Things too tedious for a Letter and which perhaps may fall into Ill hands, for I know there are many at Boston who dont Scruple to Open any Persons letters, but they are well known here.” - Dr. Oliver Noyes, lamenting the well-known fact that mail was often read.
This fact did not stop the mail’s popularity
Gilded Age: 1840–1950 — Privacy Becomes The Expectation
“Privacy is a distinctly modern product” - E.L. Godkin, 1890
“In The Mirror, 1890” by Auguste Toulmouche
By the time the industrial revolution began serving up material wealth to the masses, officials began recognizing privacy as the default setting of human life.
Source: Wikipedia user MattWade
“The material and moral well-being of workers depend, the health of the public, and the security of society depend on each family’s living in a separate, healthy, and convenient home, which it may purchase” - speaker at 1876 international hygiene congress in Brussels.
For the poor, however, life was still very much on display. The famous 20th-century existentialist philosopher Jean Paul-Satre observed the poor streets of Naples:

Crowded apartment dwellers spill on to the streets
“The ground floor of every building contains a host of tiny rooms that open directly onto the street and each of these tiny rooms contains a family…they drag tables and chairs out into the street or leave them on the threshold, half outside, half inside…outside is organically linked to inside…yesterday i saw a mother and a father dining outdoors, while their baby slept in a crib next to the parents’ bed and an older daughter did her homework at another table by the light of a kerosene lantern…if a woman falls ill and stays in bed all day, it’s open knowledge and everyone can see her.”
Insides of houses were no less cramped:

...
The “Right To Privacy “ is born
...

“The intensity and complexity of life, attendant upon advancing civilization, have rendered necessary some retreat from the world, and man, under the refining influence of culture, has become more sensitive to publicity, so that solitude and privacy have become more essential to the individual; but modern enterprise and invention have, through invasions upon his privacy, subjected him to mental pain and distress, far greater than could be inflicted by mere bodily injury.” - “The Right To Privacy” ~ December 15, 1890, Harvard Law Review.
Interestingly enough, the right to privacy was justified on the very grounds for which it is now so popular: technology’s encroachment on personal information.
However, the father of the right to privacy and future Supreme Court Justice, Louis Brandeis, was ahead of his time. His seminal article did not get much press—and the press it did get wasn’t all that glowing.
"The feelings of these thin-skinned Americans are doubtless at the bottom of an article in the December number of the Harvard Law Review, in which two members of the Boston bar have recorded the results of certain researches into the question whether Americans do not possess a common-law right of privacy which can be successfully defended in the courts." - Galveston Daily News on ‘The Right To Privacy’
Privacy had not helped America up to this point in history. Brazen invasions into the public’s personal communications had been instrumental in winning the Civil War.

A request for wiretapping.
This is a letter from the Secretary of War, Edwin Stanton, requesting broad authority over telegraph lines; Lincoln simply scribbled on the back “The Secretary of War has my authority to exercise his discretion in the matter within mentioned. A. LINCOLN.”
It wasn’t until the industry provoked the ire of a different president that information privacy was codified into law. President Grover Cleveland had a wife who was easy on the eyes. And, easy access to her face made it ideal for commercial purposes.

The rampant use of President Grover Cleveland’s wife, Frances, on product advertisements, eventually led to the one of the nation’s first privacy laws. The New York legislature made it a penalty to use someone’s unauthorized likeness for commercial purposes in 1903, for a fine of up to $1,000.
Indeed, for most of the 19th century, privacy was practically upheld as a way of maintaining a man’s ownership over his wife’s public and private life — including physical abuse.
“We will not inflict upon society the greater evil of raising the curtain upon domestic privacy, to punish the lesser evil of trifling violence”- 1868, State V. Rhodes, wherein the court decided the social costs of invading privacy was not greater than that of wife beating.

...
The Technology of Individualism
The first 150 years of American life saw an explosion of information technology, from the postcard to the telephone. As each new communication method gave a chance to peek at the private lives of strangers and neighbors, Americans often (reluctantly) chose whichever technology was either cheaper or more convenient.
Privacy was a secondary concern.

"There is a lady who conducts her entire correspondence through this channel. She reveals secrets supposed to be the most pro- found, relates misdemeanors and indiscretions with a reckless disregard of the consequences. Her confidence is unbounded in the integrity of postmen and bell-boys, while the latter may be seen any morning, sitting on the doorsteps of apartment houses, making merry over the post-card correspondence.” - Editor, the Atlantic Monthly, on Americas of love of postcards, 1905.
Even though postcards were far less private, they were convenient. More than 200,000 postcards were ordered in the first two hours they were offered in New York City, on May 15, 1873.
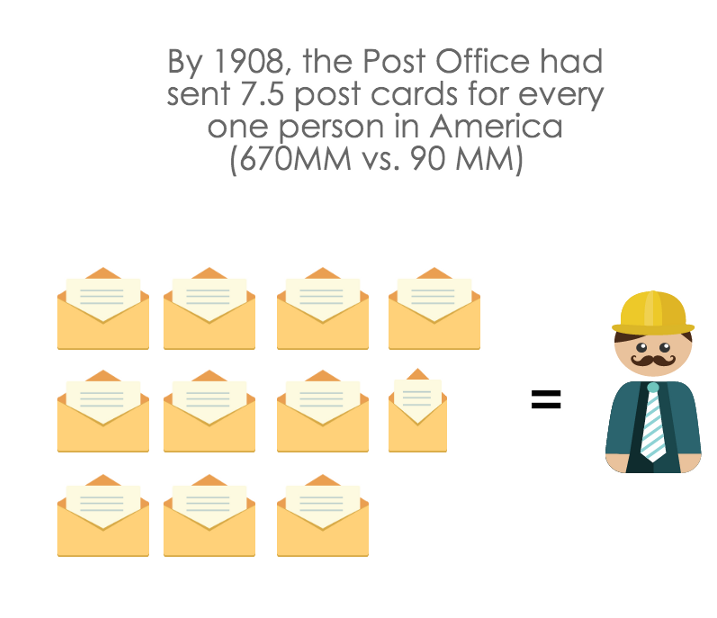
Source: American Privacy: The 400-year History of Our Most Contested Right
...
The next big advance in information technology, the telephone, was a wild success in the early 20th century. However, individual telephone lines were prohibitively expensive; instead, neighbors shared one line, known as “party lines.” Commercial ads urged neighbors to use the shared technology with “courtesy”.

But, as this comic shows, it was common to eavesdrop.

“Party lines could destroy relationships…if you were dating someone on the party line and got a call from another girl, well, the jig was up. Five minutes after you hung up, everybody in the neighborhood — including your girlfriend — knew about the call. In fact, there were times when the girlfriend butted in and chewed both the caller and the callee out. Watch what you say.” - Author, Donnie Johnson.
...

Where convenience and privacy found a happy co-existence, individualized gadgets flourished. Listening was not always an individual act. The sheer fact that audio was a form of broadcast made listening to conversations and music a social activity.
This all changed with the invention of the headphone.

“The triumph of headphones is that they create, in a public space, an oasis of privacy”- The Atlantic’s libertarian columnist, Derek Thompson.

Late 20th Century — Fear of a World Without Privacy
By the 60's, individualized phones, rooms, and homes became the norm. 100 years earlier, when Lincoln tapped all telegraph lines, few raised any questions. In the new century, invasive surveillance would bring down Lincoln’s distant successor, even though his spying was far less pervasive.

Upon entering office, the former Vice-President assured the American people that their privacy was safe.
“As Vice President, I addressed myself to the individual rights of Americans in the area of privacy…There will be no illegal tappings, eavesdropping, bugging, or break-ins in my administration. There will be hot pursuit of tough laws to prevent illegal invasions of privacy in both government and private activities.” - Gerald Ford.
Justice Brandeis had finally won

2,000 A.D. and beyond — a grand reversal
In the early 2,000s, young consumers were willing to purchase a location tracking feature that was once the stuff of 1984 nightmares.
“The magic age is people born after 1981…That’s the cut-off for us where we see a big change in privacy settings and user acceptance.” - Loopt Co-Founder Sam Altman, who pioneered paid geo-location features.
...
https://www.youtube.com/watch?v=ew94okDkCwU
...
The older generations’ fear of transparency became a subject of mockery.
“My grandma always reminds me to turn my GPS off a few blocks before I get home “so that the man giving me directions doesn’t know where I live.” - a letter to the editor of College Humor’s “Parents Just Don’t Understand” series.
...
Increased urban density and skyrocketing rents in the major cities has put pressure on communal living.

A co-living space in San Francisco / Source: Sarah Buhr, TechCrunch
“We’re seeing a shift in consciousness from hyper-individualistic to more cooperative spaces…We have a vision to raise our families together.” - Jordan Aleja Grader, San Francisco resident
At the more extreme ends, a new crop of so-called “life bloggers” publicize intimate details about their days:

Blogger Robert Scoble takes A picture with Google Glass in the shower
At the edges of transparency and pornography, anonymous exhibitionism finds a home on the web, at the wildly popular content aggregator, Reddit, in the aptly titled community “Gone Wild”.

SECTION II:
How privacy will again fade away
For 3,000 years, most people have been perfectly willing to trade privacy for convenience, wealth or fame. It appears this is still true today.
AT&T recently rolled out a discounted broadband internet service, where customers could pay a mere $30 more a month to not have their browsing behavior tracked online for ad targeting.
“Since we began offering the service more than a year ago the vast majority have elected to opt-in to the ad-supported model.” - AT&T spokeswoman Gretchen Schultz (personal communication)
Performance artist Risa Puno managed to get almost half the attendees at an Brooklyn arts festival to trade their private data (image, fingerprints, or social security number) for a delicious cinnamon cookie. Some even proudly tweeted it out.
...
twitter.com/kskobac/status/515956363793821696/photo/1 > "Traded all my personal data for a social media cookie at #PleaseEnableCookies by @risapuno #DAF14" @kskobac
...
Tourists on Hollywood Blvd willing gave away their passwords to on live TV for a split-second of TV fame on Jimmy Kimmel Live. > https://www.youtube.com/watch?v=opRMrEfAIiI
Even for holdouts, the costs of privacy may be too great to bear. With the advance of cutting-edge health technologies, withholding sensitive data may mean a painful, early death.
For instance, researchers have already discovered that if patients of the deadly Vioxx drug had shared their health information publicly, statisticians could have detected the side effects earlier enough to save 25,000 lives.
As a result, Google’s Larry Page has embarked on a project to get more users to share their private health information with the academic research community. While Page told a crowd at the TED conference in 2013 that he believe such information can remain anonymous, statisticians are doubtful.
"We have been pretending that by removing enough information from databases that we can make people anonymous. We have been promising privacy, and this paper demonstrates that for a certain percent of a population, those promises are empty”- John Wilbanks of Sage Bionetworks, on a new academic paper that identified anonymous donors to a genetics database, based on public information
Speaking as a statistician, it is quite easy to identify people in anonymous datasets. There are only so many 5'4" jews living in San Francisco with chronic back pain. Every bit of information we reveal about ourselves will be one more disease that we can track, and another life saved.
If I want to know whether I will suffer a heart attack, I will have to release my data for public research. In the end, privacy will be an early death sentence.
Already, health insurers are beginning to offer discounts for people who wear health trackers and let others analyze their personal movements. Many, if not most, consumers in the next generation will choose cash and a longer life in exchange for publicizing their most intimate details.
What can we tell with basic health information, such as calories burned throughout the day? Pretty much everything.
With a rudimentary step and calorie counter, I was able to distinguish whether I was having sex or at the gym, since the minute-by-minute calorie burn profile of sex is quite distinct (the image below from my health tracker shows lots of energy expended at the beginning and end, with few steps taken. Few activities besides sex have this distinct shape)
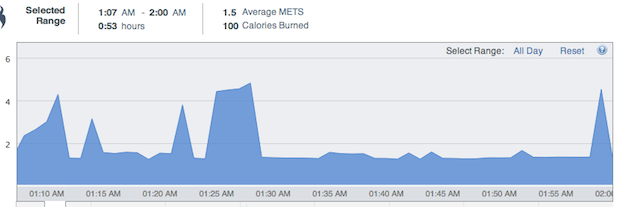
My late-night horizontal romp, as measured by calories burned per minute
...
More advanced health monitors used by insurers are coming, like embedded sensors in skin and clothes that detect stress and concentration. The markers of an early heart attack or dementia will be the same that correspond to an argument with a spouse or if an employee is dozing off at work.
No behavior will escape categorization—which will give us unprecedented superpowers to extend healthy life. Opting out of this tracking—if it is even possible—will mean an early death and extremely pricey health insurance for many.
If history is a guide, the costs and convenience of radical transparency will once again take us back to our roots as a species that could not even conceive of a world with privacy.
It’s hard to know whether complete and utter transparency will realize a techno-utopia of a more honest and innovative future. But, given that privacy has only existed for a sliver of human history, it’s disappearance is unlikely to doom mankind. Indeed, transparency is humanity’s natural state.
Friday, May 10. 2013
Brooklyn Developer Offers Up His Personal Data on Kickstarter
-----
A man had data mined himself so he can fund an app that helps others sell their own personal data.
Software developer Federico Zannier has data-mined himself, and now he’s raising money on Kickstarter to build an iPhone app and Chrome browser extension so that others can easily do the same.
Fork over $2 to the campaign and you get a day’s worth of the 1.5 gigabytes of text and 30,000 photos he’s collected from his online activities since February. That means a fun-filled 24-hours of websites, screenshots, webcam images, cursor movements, app logs, and GPS locations he’s tracked.
Is it a bargain? No, not at all—and that’s his point.
Today, companies on the web track him and everyone else and make billions selling the data. By violating his own privacy, as he puts it, he hopes that he can collect some of this value.
“If more people do the same, I’m thinking marketers could just pay us directly for our data. It might sound crazy, but so is giving all our data away for free,” he writes.
Zannier is not the first to dream up such an idea (see “A Dollar for Your Data”). One problem is that the data isn’t worth much on its own to marketers. They want to buy in bulk. That’s why Facebook and Google can make so much money. They can group people together that marketers want to reach.
So though its hard to imagine what his data is good for on its own, already with 68 backers he’s exceeded his modest funding goal of $500 for his project. If he’s successful in getting lots of people to use his data mining app, though, maybe he’ll become the next of the big data brokers.
MIT Technology Review is now exploring the issues Zannier raises in this month’s Business Report series “Big Data Gets Personal.” These articles discuss one important point that gets lost when people like Zannier dicuss their dissatisifaction with giving away their data for free: Though people are giving up more of their data than ever before, they are also getting more and more value back (see “The Data Made Me Do It.”).
Personal comment:
More and more societal questions around data... In this case, a new "business model": opening up one's own personal data (you are the product!), possibly crowd fund a mining system that would gather them from other people who act in the same way and do at best a fraction of the mining job Facebook or others could do, then get financially rewarded for breaking up one's own privacy... Instead of big corps. who do the same.
Wednesday, May 08. 2013
Stephen Wolfram on Personal Analytics
-----
The creator of the Wolfram Alpha search engine explains why he thinks your life should be measured, analyzed, and improved.

Personal control: Stephen Wolfram created the search engine Wolfram Alpha
Don’t be surprised if Stephen Wolfram, the renowned complexity theorist, software company CEO, and night owl, wants to schedule a work call with you at 9 p.m. In fact, after a decade of logging every phone call he makes, Wolfram knows the exact probability he’ll be on the phone with someone at that time: 39 percent.
Wolfram, a British-born physicist who earned a doctorate at age 20, is obsessed with data and the rules that explain data. He is the creator of the software Mathematica and of Wolfram Alpha, the nerdy “computational knowledge engine” that can tell you the distance to the moon right now, in units including light-seconds.
Now Wolfram wants to apply the same techniques to people’s personal data, an idea he calls “personal analytics.” He started with himself. In a blog post last year, Wolfram disclosed and analyzed a detailed record of his life stretching back three decades, including documents, hundreds of thousands of e-mails, and 10 years of computer keystrokes, a tally of which is e-mailed to him each morning so he can track his productivity the day before.
Last year, his company released its first consumer product in this vein, called “Personal Analytics for Facebook.” In under a minute, the software generates a detailed study of a person’s relationships and behavior on the site. My own report was revealing enough. It told me which friend lives at the highest latitude (Wicklow, Ireland) and the lowest (Brisbane, Australia), the percentage who are married (76.7 percent), and everyone’s local time. More of my friends are Scorpios than any other sign of the zodiac.
It looks just like a dashboard for your life, which Wolfram says is exactly the point. In a phone call that was recorded and whose start and stop time was entered into Wolfram’s life log, he discussed why personal analytics will make people more efficient at work and in their personal lives.
What do you typically record about yourself?
E-mails, documents, and normally, if I was in front of my computer, it would be recording keystrokes. I have a motion sensor for the room that records when I pace up and down. Also a pedometer, and I am trying to get an eye-tracking system set up, but I haven’t done that yet. Oh, and I’ve been wearing a sensor to measure my posture.
Do you think that you’re the most quantified person on the planet?
I couldn’t imagine that that was the case until maybe a year ago, when I collected together a bunch of this data and wrote a blog post on it. I was expecting that there would be people who would come forward and say, “Gosh, I’ve got way more than you.” But nobody’s come forward. I think by default that may mean I’m it, so to speak.
You coined this term “personal analytics.” What does it mean?
There’s organizational analytics, which is looking at an organization and trying to understand what the data says about its operation. Personal analytics is what you can figure out applying analytics to the person, to understand the operation of the person.
Why have you been analyzing Facebook data?
We are trying to feel out the market for personal analytics. Most people are not recording all their keystrokes like I am. But the one thing they are doing is leaving lots of digital trails, including on Facebook, and that is one of the pieces we’ve been experimenting with.
We’ve accumulated a lot of Facebook data—you’re seeing the story of people’s lives, played out in the level of data. You can see relationship status as a function of age, or the evolution of the clustering of friends at different ages. It’s really quite fascinating to see how all this stuff is just right there in the data.
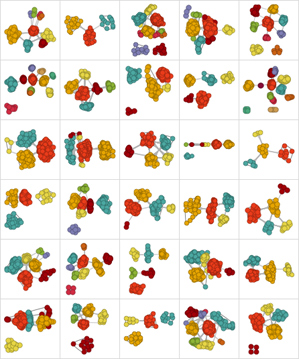
Social grid: People’s friend networks on Facebook are presented as cluster diagrams.
Isn’t a lot of what you find kind of obvious? Like friends from college aren’t connected to the ones from grammar school?
Yes, but then you get a case where the data analysis is buggy. You get some curve, and your reaction is, “Oh, yeah, I understand why the curve is that way, I’ve got an argument for it.” But then, oops, there was a bug in the analysis and actually the curve is something different. That reminds you things aren’t quite so obvious. If you actually measure it, that’s doing science.
What’s the connection to the search engine you built?
Right now Wolfram Alpha is strong on public knowledge: accumulating and searching the knowledge of the civilization. But what you have to do in personal analytics is try to accumulate the knowledge of a person’s life. Then the two can actually be integrated, and I’ll give a kind of silly example. You might ask: “Who do I know that can go out into their backyard and go and look at the night sky right now?” For that you have to be able to compute who is in nighttime, who doesn’t have cloudy weather, and things like this. And we can compute all that stuff.
What do you see as the big applications in personal analytics?
Augmented memory is going to be very important. I’ve been spoiled because for years I’ve had the ability to search my e-mail and all my other records. I’ve been the CEO of the same company for 25 years, and so I never changed jobs and lost my data. That’s something that I think people will just come to expect. Pure memory augmentation is probably the first step.
The next is preëmptive information delivery. That means knowing enough about people’s history to know what they’re going to care about. Imagine someone is reading a newspaper article, and we know there is a person mentioned in it that they went to high school with, and so we can flag it. I think that’s the sort of thing it’s possible to dramatically automate and make more efficient.
Then there will be a certain segment of the population that will be into the self-improvement side of things, using analytics to learn about ourselves. Because we may have a vague sense about something, but when the pattern is explicit, we can decide, “Do we like that behavior, do we not?” Very early on, back in the 1990s, when I first analyzed my e-mail archive, I learned that a lot of e-mail threads at my company would, by a certain time of day, just resolve themselves. That was a useful thing to know, because if I jumped in too early I was just wasting my time.
What technologies are needed to do personal analytics at a large scale?
It’s data science and the whole cluster of technologies that come with that. Then it’s having computational knowledge about the world and being able to make queries in natural language. Then you need to sense things about the world, whether it’s with sensors or being able to do visual recognition to know what one is seeing. Then the final thing is just all the plumbing infrastructure to get all of these devices to communicate and feed their information to a place where one can do analysis.
Where do you stand on commercializing these ideas?
The personal analytics of Facebook for Wolfram Alpha is a deployed project, and there will be more of those in the personal-analytics space. We think we can do terrific things, but you have to be able to get to the data. That has been the holdup. The data isn’t readily available. Recently we’ve been working with different companies to try and make sure we can connect their sensors to kind of a generic analytics platform, to take people’s data, move it to the cloud, and do analytics on it.
How much better do you think that people or organizations can become with some data feedback?
I think it will be fairly dramatic. It’s like asking how much more money can you make if you track your portfolio rather than just vaguely remembering what investments you made.
Related Links:
Tuesday, September 18. 2012
Camouflage from Computer Vision
An interesting work by Adam Harvey about camouflage from computer vision (even though if the piuctures below look like photoshop demo). Which could lead to new type of haircut and makup when Facebook's identifying (surevillance) camera will be displayed all over the place, in shopping areas and franchised spaces.

See more of it on the project's website, with additionnal picture: CV Dazzle.
Tuesday, May 18. 2010
Facebook Personal Data a Security Risk
Last month, Facebook finally crossed a line. The company announced that it would make certain user information--including a user's name, hometown, education, work, and "likes" and "dislikes"--permanently public.
Facebook's default privacy policy has gradually shifted to expose more user data to the wider Web, but the reaction to this latest change has been significant. Last week, a collection of European data-protection authorities known as the Article 29 Working Group sent Facebook a letter chastising the company for not allowing users to limit access to their social data. The letter follows a similar criticism of Facebook by several members of congress, such as Sen. Charles Schumer, D-NY, over the past month. The reaction from privacy advocacy groups, and from many of Facebook's users, has also been vocal.
Some experts also say that the increase in information disclosure could have a serious side-effect--opening up new opportunities for hackers. Kevin Johnson, a senior researcher with security firm InGuardians, uses Facebook as a starting point for his job: testing companies' network security. Many times, he says, the most significant vulnerabilities are not in hardware or software, but in a users' use of social networks. The information leaked on social networking sites can be used to impersonate a legitimate person, in order to recover a password, for example; or to trick users into opening a malicious file by making it appear to come from a friend or a colleague.
"As a penetration tester--as an attacker--Facebook's privacy settings have made my job easier," Johnson says. "In the past, before two years ago, we had to trick people into running a [rogue] application [to collect data]. Now, the majority of people out there--the bulk of Facebook--run under default privacy settings."
Pushed by a need to monetize the data entered by users, Facebook has increasingly loosened its privacy policies. In 2005, the company's original policy stated that no information would be shared with people "who [do] not belong to at least one of the groups specified by you in your privacy settings." By 2010, the policy had changed to one that focuses on sharing much more information, stating that applications and Web sites "will have access to General Information about you." The text of the company's privacy policy has grown nearly 500 percent and users are now required to navigate some 50 different privacy settings.
"Facebook says that they are introducing more privacy settings because they want to give users more control, but what they have done is make things more confusing," says Fred Stutzman, a privacy researcher and PhD candidate at the University of North Carolina at Chapel Hill. "Over time they have made changes that make people's information more open, because that is how they drive the use of the network."
"This is something that is different from how Facebook had been operating," says Kurt Opsahl, a senior staff attorney with the Electronic Frontier Foundation. "In the past, they encouraged sharing that information, but now they have taken information that many people consider private and made it public, and they did so in a very heavy-handed way."
Yet, as Facebook has grown, users have become savvier about their data security, Stutzman says. Students at UNC Chapel Hill, for example, have increasingly opted to set their Facebook privacy to the highest possible setting, with almost 60 percent of students using the "Friends Only" setting in 2008 compared with less than 20 percent in 2005. Stutzman says that people have to overcome their preference to run under the default settings and opt not to change them.
Alessandro Acquisti, associate professor of information science and policy at Carnegie Mellon University, argues that Facebook is likely counting on that psychology to limit the number of people who ratchet up the privacy settings. "What is happening, it is almost a bait and switch technique," he says. "Every time they change the status quo, they are getting people more and more adjusted to the habit of disclosing information. If you told people five years ago that all these different fields are public, they would say, 'No way.' "
Facebook says that some information--a person's name, her network of connections, and pages that she likes and dislike have always been public. The user's photo, gender, and current city have all been added to the must-be-public profile information, the company acknowledges, but it says that only a small fraction of users are changing their settings to restrict access to information.
"The overwhelming majority of users have made all of this information available to everyone," a spokesman says. "We've found that the small percentage who have restricted any of this information have intended to prevent contact from nonfriends."
However, Facebook may not find an easy way out of the current controversy. In February 2009, when users were upset about other changes to its terms of service, the company created its Facebook Principles, a list of promises of how the company would treat its users and their data, including that "people should own their information, they should have the freedom to share it with anyone they want and take it with them anywhere they want, including removing it from the Facebook Service."
The company has failed to live up to those principles, says the EFF's Opsahl. "It is not just a matter of, can Facebook weather the storm of criticism and keep their users--they have a real situation here," Opsahl says. "But they have an opportunity as well. They can try and fix this problem and regain their users' trust."
Copyright Technology Review 2010.
Personal comment:
In connection with the post below... A question that rises now every month or two months and that is turning into a fight between "privacy" vs "publicy" advocates. I'm on the side of "open publicy" and "proprietary privacy", certainly not on the side of changing rules every two weeks for profit reasons...
Friday, May 14. 2010
Who Controls Identity on the Web?
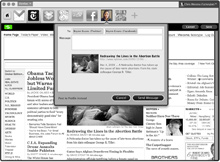 |
| Identity parade: A concept browser designed by Mozilla would let users control a single identity for logging in to different websites. Credit: Mozilla Foundation |
The two approaches are fundamentally different. Facebook's Open Graph Protocol uses the oAuth standard, which lets a website identify a user via a third-party site without exchanging sensitive information. Facebook--whose 400 million active users make it the world's largest social network in the world--stands to benefit as other sites come to rely on the information it holds about users and their social connections.
The approach taken by the Mozilla Foundation, which makes the Firefox browser, comes in the form of a suite of browser extensions. One of the extensions, called Account Manager, can replace all of a user's online passwords with secure, computer-generated strings that are encrypted and protected with a single master password. Mozilla's identity extensions can interact with other identity standards, including OpenGraph, oAuth, and OpenID, a standard that allows any website or Web service provider to host a social network-style profile of a user. The goal of the Mozilla Foundation's efforts is to establish a set of open standards and protocols that could be implemented in any browser or website.
As much as possible, identity would be moved out of the webpage itself and into the "chrome" of the browser--the parts around of the webpage. Logging in and out of sites would be accomplished through buttons at the top of the browser that would activate secure protocols--rendering the process of creating and memorizing usernames and passwords obsolete.
"Every user of the Internet today is expected to describe themselves to every site they go to," says Mike Hanson, principal engineer at Mozilla Labs. Inevitably, Hanson says, this leads to confusion and security holes, such as passwords that are identical across multiple sites.
The solution, according to Hanson, is to let the browser itself manage user identity. Weave Sync, another Mozilla extension, is designed to enable that vision. It stores encrypted versions of a growing list of data on a Mozilla-hosted server (or any user-specified server), including a person's history, preferences, bookmarks, and even open tabs, which can be synced across two or more browsers. This allows users to have the same browser workspace on any device that supports Firefox or its mobile equivalent, Fennec. There's even a prototype for the iPhone, built on top of Apple's Safari browser.
Last fall Mozilla Labs also commissioned Chris Messina, at the time a researcher in residence at Mozilla Labs, to design a Web browser that would manage the other half of online identity--a user's social graph. In Messina's mock-ups, a user can interact with people on the Web in ways that go beyond what OpenID or Facebook's OpenGraph currently offer. "The idea of a social browser is important to me because it's the single point of integration for all websites," says Messina. "It's the one thing that knows who you are across all social experiences."
Messina's designs envision a browser that lets users "follow" other users by viewing all of their relevant information streams--Facebook, Twitter, Flickr, etc.--collected into a single browser tab stamped with that user's profile picture. A similar interface could also be used to control exactly what personal information other people and websites have access to. This could allow, for instance, a user to change her shipping address across any number of sites at once, or to control which version of their identity a particular groups of friends can access. "I'm not interested in the [Mark] Zuckerberg approach, where privacy doesn't exist anymore," says Messina, referring to the CEO of Facebook.
Both Facebook and the Mozilla Foundation will face challenges in pushing their own vision of online identity. John Mitchell, a professor of computer science at Stanford, says the most significant barrier will be the adoption of suitable protocols. Before such protocols can be standardized and rolled into, for instance, the next version of HTML, Web developers are going to have to be willing to experiment.
"What I've seen from a lot of companies is an attempt to guess the end solution and build that only," says Mitchell. "It would be better if, instead, we had an open architecture where people could try many different approaches."
If the new Mozilla software and Messina's designs are sufficiently popular with users and developers (not to mention the influencers who sit on the boards of standards committees like the World Wide Web Consortium), then the foundation's technology could find its way into the regular release of Firefox and perhaps, ultimately, into other browsers.
To Messina, just drawing up the blueprints for such technology was an important first step. "We're further away from the death of the password than I'd like to be, but it's a nice goal to aim for," he says.
Copyright Technology Review 2010.
Personal comment:
Back in 2003 (and up to 2005), we treated this question of identity, surveillance-monitoring technique and data mining of user's data in the Knowscape Mobile project, or in the AI vs AI in self-space project too. We claimed for a total open approach of online identity considering the web as a public space (open data collected in open space belongs to everybody). Of course, this was a speculative project to address the question. An approach that won't be feasible in reality because we definitely need all type of spaces: public, private, semi-public, semi-private, etc. But the status of "space" and their data should be transparent to all users.
Today, this question of "who owns the data", of "public vs private" is becoming more and more of a hot problem, in particular regarding personal data. But it is definitely a problem worth discussing it. So as the status of public space.
Tuesday, February 23. 2010
Augmented Identity
 |
| Enhanced image: A prototype app for smart phones matches live images of people to stored profiles and shows icons for social networking sites around their heads. Credit: The Astonishing Tribe |
"It's taking social networking to the next level," says Dan Gärdenfors, head of user experience research at TAT. "We thought the idea of bridging the way people used to meet, in the real world, and the new Internet-based ways of congregating would be really interesting."
TAT built the augmented ID demo, called Recognizr, to work on a phone that has a five-megapixel camera and runs the Android operating system. A user opens the application and points the phone's camera at someone nearby. Software created by Swedish computer-vision firm Polar Rose then detects the subject's face and creates a unique signature by combining measurements of facial features and building a 3-D model. This signature is sent to a server where it's compared to others stored in a database. Providing the subject has opted in to the service and uploaded a photo and profile of themselves, the server then sends back that person's name along with links to her profile on several
"It's a very robust approach" to facial recognition, says Andrew Till, vice president of marketing solutions at Teleca, a mobile software consulting company in the United Kingdom. "It's much, much better than what I've previously seen."
Till says that applying image and face recognition to the trend of posting photos on social networking sites opens up interesting new possibilities. "You start to move into very creative ways of pulling together lots of services in a very beneficial way for personal uses, business uses, and you start to get into things that you otherwise wouldn't be able to do," he says.
Polar Rose's algorithms can run on the
Academic and company research groups have developed augmented reality applications, which superimpose virtual objects and information on top of the real world, for more than a decade. But until the past year or so, all of these prototype applications required bulky headsets and laptop computers. With more powerful sensors, cameras, and microprocessors built into mobile phones, however, augmented reality applications have begun hitting the mainstream. Several apps take advantage of the GPS chips and compasses available in newer smart phones. For example, PresseLite's Metro Paris app and Acrossair's Nearest Tube provide iPhone users with directions to nearby subway stops.
But Gärdenfors calls such applications "relatively crude." They often obscure objects with labels, he notes, and are sometimes limited by the fact that location information may not be available. He thinks that many augmented reality services could benefit from including elements of computer vision to make information retrieval and label positioning more precise. "This could absolutely work for other kinds of objects, and I think we'll see that soon," he says.
However, Gärdenfors notes that using computer vision to identify buildings and other objects holds challenges that they didn't encounter in developing the augmented ID application. "With facial recognition, it's so obvious what you want to search for," says Gärdenfors. "With other objects, it may be harder to tell which item on the screen you want to identify."
Gärdenfors says that TAT has taken potential privacy concerns with the technology seriously from the beginning. "Facial recognition can be a kind of scary thing, and you could use it for a lot of different purposes." For that reason, the company designed Recognizr as a strictly opt-in service: people would have to upload a photo and profile of themselves, and associate that with different
A concept video of the augmented ID application that TAT posted on YouTube last summer garnered a great deal of attention. Gärdenfors says the company often uses this strategy to determine which ideas justify further development. A live demonstration also received a lot of interest at the Mobile World Congress. "We're probably going to partner with some company over the next couple of months to take it to the next level and actually build [a product]," Gärdenfors says. While this will require partnerships with a device maker, a mobile service provider, and social networking services, the technology is developed enough that a commercial application could be ready in as little as a month or two, he says.
Copyright
----
Related Links:
Personal comment:
Is it good or bad news (I remember that the "recognizer" were very evil creatures in the movie Tron ;))? You still need to be part of the system and accept it (apparently) to be recognized, which is good. But if it's as hard as systems like Facebook to sign out, then you might have lost your "right to disappear" for a very long time...
It's again this question of privacy vs. "publicy". Some people prefer to live in "private mode" by default (this was the old "de facto" way of living), while others prefer the contrary.
Friday, February 05. 2010
Facebook Profile For Holocaust Victim Brings History to Life

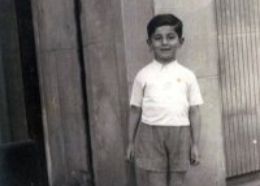 Virtual memorials are nothing new — people have been paying their respects to departed loved ones on Facebook and Myspace for years. But a Facebook page set up for Henio Zytomirski, a 6-year-old Polish boy who was killed during the Holocaust, is truly revolutionizing the way we recount history and remember the dead. His profile is, in essence, a virtual museum.
Virtual memorials are nothing new — people have been paying their respects to departed loved ones on Facebook and Myspace for years. But a Facebook page set up for Henio Zytomirski, a 6-year-old Polish boy who was killed during the Holocaust, is truly revolutionizing the way we recount history and remember the dead. His profile is, in essence, a virtual museum.
Last summer, a group of people in Lublin, Poland, and Israel — including Henio’s cousin Neta Zytomirski Avidar — created a Facebook profile for the boy, who was sent to the Majdanek death camp in 1942. According to the AP, the idea grew out of a group called Grodzka Gate-NN Teater, which uses the arts to remember victims of the Holocaust. Henio was chosen because there were so many photos and letters available to draw from, which makes his profile a truly rich reading experience.
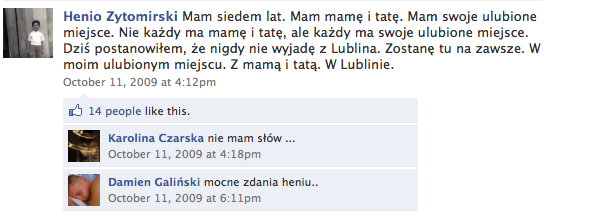
The profile functions as kind of a piecemeal storybook, with Polish status updates in Henio’s voice as well as photos and other updates in the third person that tell his tale. Henio’s own voice is simple and touching, as you can see in the selection below. (Rough Translation: “I am seven years old. I have a mom and dad. I have a favorite place. Not everyone has a mom and dad, but everyone has their favorite place. Today I decided that I will never leave Lublin. I will stay here forever. In my favorite place. With Mom and Dad. In Lublin.”)
According to the AP, not everyone is happy with the project — the news company cites Adam Kopciowski, a historian at Lublin’s Marie Curie-Sklodowska University who specializes in Jewish studies, who thinks that writing in the dead boy’s voice is ethically unsound and amounts to “abuse toward a child that has been dead for the past 70 years.” Others have also raised the fact that the page — much like Doppelganger Week — violates Facebook’s TOS.
Still, Henio’s cousin makes very clear in a note on the profile that the young boy’s voice is meant to be purely speculative, and that he is to function as a symbol:
“We try to reconstruct his life in the ghetto from survivors’ testimonies, from documents, from knowing the history of Lublin during the Nazi occupation. From all of these we try to guess what might have been his testimony.
Henio is also a representing figure, a symbolic figure, an icon. His figure represents the destruction of the ancient Jewish community of Lublin.
His figure brings to Facebook the story of the Jewish community under the Nazi occupation regime and of its ruin.”
And judging by his 3,000+ fans, scores of thankful wall posts and avalanche of virtual gifts, people have become enamored of the long-lost boy.

Aside from being a touching memorial to a tragically departed boy, Henio’s profile is also a fascinating use of social media as an educational tool. Some of us have probably visited the United States Holocaust Memorial Museum in Washington, D.C. Upon entering, you receive a passport depicting someone who experienced the Holocaust, and throughout your tour through the museum, you learn his or her fate. Henio’s page brings this experience to another level, allowing you to interact with the boy, and to learn about his life in a way that integrates fully into your own social media experience.
This profile only goes to show how sites like Facebook are no longer silly time wasters or places to troll for your next collegiate hookup, they provide us with news, entertainment, advertisements and, now — as more and more people are seeing it as both a news portal and source — education. I recently became a friend of Henio’s, will you?
-----
Via Mashable
Monday, November 23. 2009
Face recognition Phones/App will ID people on sight
Nokia is reportedly working with Korean developers on a face recognition application for some of its upcoming phones.
This application is designed to identify the faces of the person whose photos you have clicked using your mobile phone. All the user needs to do is to identify the face in his/her album just once. Post that, the application performs a search and identifies all similar looking faces stored on the phone. Apart from the face recognition capabilities, it will also feature time and location based features.
The application will make its debut with phones running Series 60 OS and having at least a 3-megapixel camera.
---
Like Nokia last week, Qualcomm has been talking up the future of phones, and the company gave us a sneak peek of what to expect a short while down the road: face recognition technology tied to social network search technology, so you can find out what a stranger just tweeted simply by pointing your handset at them. Is Facebook stalking about to get a whole lot worse?
We’ve seen in-picture face recognition start to appear in mobile phones recently, with Sony Ericsson promising the tech will make it into the Xperia X10 early next year. But Qualcomm reckons it’s going to get much more integrated and advanced.
Qualcomm Snapdragon tablet concept revealed
Gilbert admitted that the possibility raised serious privacy issues – you could theoretically pull up a person’s home address through automatic whois requests – but ethics aside, it’s an interesting next step for augmented reality apps, which layer data over the surroundings and have started to take off in a big way over the last year. As phones get faster and more powerful, what’s to stop people integrating this form of search?
---
Apple iPhoto
---
Face.com is opening its photo-tagging system, based on facial-recognition technology, to Facebook members.
- Face.com
- Face.com’s Photo Tagger app uses facial-recognition technology to help Facebook members tag photos of their friends.
Photo Tagger, which launched to a limited group of users in July, scans a user’s photo albums on the social-networking site, then lets him tag faces it identifies. It groups multiple shots of each person, making it easy to tag large albums, and users can also adjust or remove incorrectly tagged pictures.
Once a member has been identified, the app prompts him or her to approve the tag — a crucial privacy step, since he or she may not want to be labeled in a photo. It also works with a member’s current photo-privacy settings on Facebook.
For users with lots of friends and photos, Photo Tagger helps them spread the word and ensure that their contacts see relevant shots on their news feeds, said Gil Hirsch, Face.com’s chief executive.
“If you don’t tag an album, people don’t know about it,” he said. “What we’re doing is basically supporting the existing mechanism and augmenting it.”
The Tel Aviv-based company’s facial-recognition technology specializes in pictures in which the subject isn’t looking at the camera, as well as low-resolution or out-of-focus images, “what we refer to as everyday photos,” Mr. Hirsch said. “All these different things that make photos real.”
Photo Tagger is free, though he said Face.com is considering fee-based services that it could provide over the system. He declined to say what they might be.
Face.com is also introducing a new Photo Tagger feature, dubbed Face Alerts, along with the launch. It allows members to be notified through Facebook or email when new public photos are uploaded of them or their friends. “It’s a Google Alerts for faces,” Mr. Hirsch said, and a way for members to gain more control over where their image appears.
The app has taken off even in its alpha phase — he said more than 35,000 people have tried it. TechCrunch called it a “time vampire” because of its addictive nature, though VentureBeat noted that it might even work too well, and that it could lead to more people tweaking their privacy settings to avoid the limelight.
Mr. Hirsch said the company is sensitive to privacy concerns. “While for some folks face-recognition technology feels a little creepy, we’ve had no complaints or direct issues with the applications,” he added. “In fact, we’ve had quite a few privacy-aware users who tried out our apps, and their feedback was very positive, and with the new Face Alerts feature felt it actually helps them gain control of their online image.”
Personal comment:
A set of articles concerning the same facial detection and recognition schemas. It seems to be available/coming soon on social networks, normal computer applications and mobile phones with bridges from one platform to another. Pushing this technology to the dark side will make possible to any one of us to be able to obtain the name, the address, or any kind of data about a person we can just see in the street, just by taking a simple picture. As the technology seems to be planned for huge deployment, people will be able to file/record their own personal/biometric data on any kind of devices/social networks, prior to any possible reaction of legal instances.
fabric | rblg
This blog is the survey website of fabric | ch - studio for architecture, interaction and research.
We curate and reblog articles, researches, writings, exhibitions and projects that we notice and find interesting during our everyday practice and readings.
Most articles concern the intertwined fields of architecture, territory, art, interaction design, thinking and science. From time to time, we also publish documentation about our own work and research, immersed among these related resources and inspirations.
This website is used by fabric | ch as archive, references and resources. It is shared with all those interested in the same topics as we are, in the hope that they will also find valuable references and content in it.
Quicksearch
Categories
Calendar
|
|
July '25 | |||||
| Mon | Tue | Wed | Thu | Fri | Sat | Sun |
| 1 | 2 | 3 | 4 | 5 | 6 | |
| 7 | 8 | 9 | 10 | 11 | 12 | 13 |
| 14 | 15 | 16 | 17 | 18 | 19 | 20 |
| 21 | 22 | 23 | 24 | 25 | 26 | 27 |
| 28 | 29 | 30 | 31 | |||
