Friday, June 26. 2009
Gates approves creation of new cyber command
WASHINGTON (AP) -- Defense Secretary Robert Gates formally ordered the creation Tuesday of a new military cyber command that will coordinate the Pentagon's efforts to defend its networks and conduct cyberwarfare.
A three-page memo signed by Gates orders U.S. Strategic Command to begin plans to set up a subcommand and be prepared to provide an implementation plan by Sept. 1, and begin initial operation no later than October.
Officials have said the new command would be located at Fort Meade in Maryland, and would be fully ready to go by the end of next year. Gates said in his memo that he is recommending that the director of the National Security Agency -- currently Lt. Gen. Keith Alexander -- be tapped to lead the command, in a dual role with his current responsibilities. That job would be upgraded to a four-star general slot.
"Our increasing dependency on cyberspace, alongside a growing array of cyber threats and vulnerabilities, adds a new element of risk to our national security," said Gates in the memo, which was obtained by The Associated Press.
He added that the new command "must be capable of synchronizing warfighting effects across the global security environment as well as providing support to civil authorities and international partners."
While the reorganization is just beginning, one senior defense official said the command is not expected to be very large. It would likely involve hundreds, rather than thousands of employees, the official said, speaking on condition of anonymity to discuss internal decisions.
The low-key launch of the new military unit reflects the Pentagon's fear that the military might be seen as taking control over the nation's computer networks.
Creation of the command, said Deputy Defense Secretary William Lynn at a recent meeting of cyber experts, "will not represent the militarization of cyberspace."
Lynn said the focus of the command will be on the military's 15,000 networks and its seven million computers, noting that commanders depend on those systems in battle. The military, he said, needs to be able to respond to any intrusion or attack "at network speed."
Rep. Howard "Buck" McKeon, R-Calif., ranking Republican on the House Armed Services Committee, said he was pleased with the move to increase the military's capabilities in cyberspace, and he urged the Pentagon to work with lawmakers as plans progress. House and Senate members have been working on legislation aimed at bolstering the nation's cyber coordination.
Pentagon officials have stressed in recent weeks that the cyber command will not infringe on the Department of Homeland Security, which is the lead agency for other federal digital systems.
President Barack Obama has announced plans to name a cyber coordinator for the White House, in order to better coordinate the nation's efforts to protect critical computer networks and work more closely private industry, which owns or controls key financial, electrical and other systems.
The U.S., Obama said earlier this month, is not as prepared as it should be to face threats of cyber espionage or other attacks.
Government and military officials have acknowledged that U.S. computer networks are constantly assailed by attacks and scans, ranging from nuisance hacking to more nefarious probes and attacks. Some suggest that the actions at times are a form of cyber espionage from other nations, such as China.
Officials earlier this year disclosed that there was an attack against the electrical grid, and computers at the Pentagon were infected by a virus.
On the Net:
Defense Department: http://www.defenselink.mil
Copyright 2009 The Associated Press.
Copyright Technology Review 2009.
-----
Personal comment:
Terme de science-fiction il y a encore 15 ou 20 ans, la "cyberwar" devient effective et la création de ce centre de commande US entérine le fait que l'on co-existe désormais avec l'univers "virtuel", avec tous les mashups que cela peut induire (dont celui-ci, pas le plus alléchant...)
Thursday, June 25. 2009
EU Wants Tighter Privacy on Social Networks
 Are social networks such as Facebook and MySpace doing enough to protect their users’ privacy? In the European Union, they might need to do more. A panel of European regulators has laid out operating guidelines for social networks, which will ensure their compliance with strict – albeit sometimes vague – online privacy laws in the European Union.
Are social networks such as Facebook and MySpace doing enough to protect their users’ privacy? In the European Union, they might need to do more. A panel of European regulators has laid out operating guidelines for social networks, which will ensure their compliance with strict – albeit sometimes vague – online privacy laws in the European Union.
These laws mostly stem from the European Union Directive on Data Protection of 1995, which, among other regulations, prohibits collection of personal information without consumers’ permission, forbids employers to read workers’ private e-mail, and doesn’t allow companies to share personal information on users without their permission.
However, according to data-privacy lawyer Jan Dhont at Lorenz in Brussels, these regulations aren’t always very clear. For example, the companies that collect personal information must use it for “legitimate purposes,” which can be interpreted in many different ways.
Nevertheless, the guidelines that were laid out will require quite a bit of effort from sites such as Facebook and MySpace, who cannot neglect their European user base and will therefore surely at least try to comply to avoid clashing with the EU regulators.
According to the guidelines, social networks must set security settings to high by default; they must allow users to limit data disclosed to third parties, and they must limit the use of sensitive information (race, religion, political views) in behavioral advertising.
Furthermore, social networks must delete accounts that have been inactive for long periods, as well as discard users’ personal information after they delete their accounts; an interesting regulation in view of the recent Facebook scandal, in which Facebook claimed ownership of all the content you’ve ever uploaded even if you quit the service. Facebook later apologized and restored their previous Terms of Service, even letting users be part of the decision process in creating the new ToS. However, it must be noted that even if this sounds like democracy, it’s a frail one, as Facebook still sets up the stage and has the last word on every decision.
It is therefore good that there’s an overseer, looking over our online privacy and security. These latest guidelines from the European Union will definitely make life harder for social networks such as Facebook and MySpace, but will most likely have a positive impact on user privacy in the long run.
You can read the entire set of guidelines created by the Article 29 Data Protection Working Party in PDF format here.
-----
Vis Mashable
Personal comment:
De façon générale, la thématique de la privacité monte dans les médias, l'intérêt du public aussi et la législation tente de suivre...
Tuesday, June 23. 2009
Traveling the Web Together
 |
| Credit: Technology Review |
Researchers from the College of William and Mary, in Williamsburg, VA, hope to change that with software called RCB (for real-time collaborative browsing) that makes it far simpler to connect with another person as he or she clicks around the Web.
There are already a few ways to navigate through Web pages collaboratively, but each has its limitations. Trailfire, for example, lets a user record her Web sessions but doesn't allow users to browse together at the same time. Another service, called Weblin, provides a way to annotate sites with animations and avatars, but it is only geared toward interacting on a single Web page. More powerful "screen sharing" lets users browse together as if sharing the same machine, but this normally involves connecting to an outside server.
What sets RCB apart, says Haining Wang, an assistant professor of computer science at William and Mary, is its simplicity. Only the person leading a session needs to have a browser extension installed--others can then participate with any standard Web browser. "This makes cobrowsing very simple and practical," Wang says. The researchers suggest that RCB could be particularly useful for businesses offering customer support, for distance-learning courses, or for friends who want to share links.
To use RCB, one person has to install a Firefox browser extension. This allows her to generate a session URL that can be sent to other participants. When a second user clicks on the URL, the host's RCB extension sends him to a Web page that then connects him to the first person's browser. Once connected, both users can interact with a Web page and follow links, with all actions funneled through the host's browser. The host also retains control over the session and can add or remove participants as needed. A host can connect to up to 10 participants without losing too much performance, but the researchers say that RCB is best suited for two people at a time.
"There is a real desire by users to share URLs with collaborators in real time," says Meredith Ringel Morris, a computer scientist in the adaptive systems and interaction group at Microsoft Research, who launched a collaborative search tool called SearchTogether last year. A survey conducted by Morris in 2006 found that 30 percent of participants said that they had tried to browse with others using instant messaging.
Morris says that the researchers' efforts to simplify cobrowsing through RCB "are a big step in the right direction." Users with limited technical skills could especially benefit from a cobrowsing tool, Morris says, since it allows a more experienced Internet user to walk them through unfamiliar tasks. Because this needs to be easy to do, she says, it's important that RCB uses a regular Web browser.
On the other hand, Morris worries that RCB places too much of a burden on the host of a cobrowsing session. As the system is currently implemented, a user can only set up a session if she knows her computer's host name or Internet protocol (IP) address, as well as the number of an unused transmission control protocol (TCP) port.
Vladimir Estivill-Castro, a professor at the School of Information and Communication Technology at Griffith University, in Australia, who has studied the usability of cobrowsing tools, says that the approach "seems rather convenient." But he thinks that more work needs to be done to improve the system so that many users can take actions on a single Web page.
RCB is not yet available to the public, but the researchers presented their work last week at the Usenix Technical Conference, in San Diego. Wang says that his group filed a provisional patent last September with the hope of getting the technology adopted by major browser vendors.
Copyright Technology Review 2009.
-----
Personal comment:
Ca ne vous fait penser à rien? Knowscape? (qui allait d'ailleurs plus loin en terme de concepts)
Friday, June 19. 2009
Global Net Traffic Reveals Iran's Censorship Surge
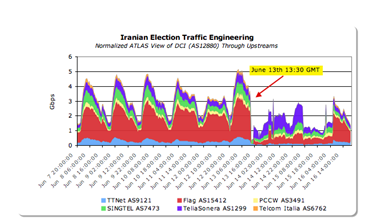
Iran's government might not have completely cut off Internet access within its borders, as have other governments suffering from political unrest. However, new evidence shows that the Data Communication Company of Iran (DCI) has been manipulating the overall flow of traffic to the country, according to Craig Labovitz, chief scientist for Arbor Networks, a company based in Chelmsford, MA, that provides network security and analysis for many Internet service providers and large businesses.
Although Labovitz has no information directly from Iran, he has based his conclusions about Iranian traffic on data collected from more than 100 Internet service providers that together allow Arbor Networks to form a picture of global Web traffic.
 |
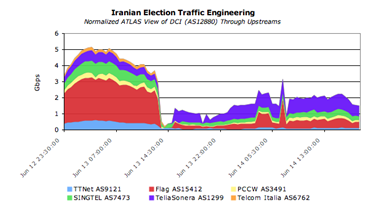 |
Labovitz found that on June 13, the day after elections, Iranian traffic fell off almost completely. Traffic came back a few hours later, he writes, though just a little. By June 16, Labovitz says, it was back to about 70 percent of normal.
Labovitz writes,
So what is happening to Iranian traffic?
I can only speculate. But DCI's Internet changes suggest piecemeal migration of traffic flows. Typically off the shelf / inexpensive Internet proxy and filtering appliances can support 1 Gbps or lower. If DCI needed to support higher throughput (say, all Iranian Internet traffic), then redirecting subsets of traffic as the filtering infrastructure comes online would make sense.
Unlike Burma, Iran has significant commercial and technological relationships with the rest of the world. In other words, the government cannot turn off the Internet without impacting business and perhaps generating further social unrest. In all, this represents a delicate balance for the Iranian government and a test case for the Internet to impact democratic change.
-----
Via MIT Technology Review (blogs)
Thursday, June 18. 2009
The Web vs. the Republic of Iran
 |
| Tweet: Mousavi1388's Twitter feed allows the opposition party to share information. Credit: Technology Review |
Attempts to censor the press have increased significantly since last Friday's disputed election. Yesterday, press credentials for foreign journalists were revoked, and many were told via phone and fax not to report from the streets. Other journalists have been injured, detained, or arrested by the authorities.
Yet despite the media crackdown, information continues to leak out of Iran via social networking, microblogging, and photo- and video-hosting websites. These resources have been used before to organize during political crises--in Georgia and Russia, Burma and Kenya--but the sheer scale and scope are striking in Iran's case.
Ethan Zuckerman, of the Berkman Center for Internet and Society, at Harvard University, and cofounder of the blogger advocacy group Global Voices, says that people inside Iran who are blogging, Tweeting, and sharing photos are "doing an amazing job of making this political movement visible to the world." Photo and video sharing, in particular, have brought the situation home to foreign observers and have made it "much more real, and much more real time," Zuckerman says.
Zuckerman attributes the continued information flow in part to "latent capability": savvy Internet users in Iran already know how to circumvent blocking measures, so in a political upheaval they don't have to relearn the process. "The longer a country censors and the more aggressively it censors," says Zuckerman, "the more incentive it gives citizens to learn how to get around that." Because Iran has been filtering since at least 2004, says Zuckerman, a lot of Iranians already know how to use proxies--computers that route traffic around a government-imposed block. So even if you're just using a proxy to surf porn, says Zuckerman, suddenly, a political crisis hits and you already have the means to communicate.
Normally, Iran's government maintains a tight grip on Internet use. Because Iran is economically ostracized, the government doesn't have many business relationships that it can leverage to prompt censorship from the outside--unlike China, for example, which runs a censored version of Google (and its ads) through its state-controlled filters. But communications from Iranian ISPs serving the public, rather than academic institutions or private businesses, are all routed through the state-controlled Telecommunication Company of Iran (TCI), allowing for easy filtering. Blogs and websites dedicated to anti-Islamic and anti-government content are routinely blocked. Facebook was blocked sporadically in the months leading up to Friday's election and during the election itself, as were websites for the major opposition candidates and several pro-reform sites. Facebook and YouTube are still blocked in response to the post-election protests.
Having reportedly purchased an electronic surveillance system for Internet monitoring in 2008, the Iranian government is well equipped to handle tracking and recording through its centralized system. According to a just-released report from the Open Net Initiative (ONI)--a project involving researchers from Harvard University, the University of Toronto, the University of Cambridge, and the University of Oxford--this has already occurred with women's-rights activists who were arrested and reportedly shown transcripts of their IM sessions.
In the past, the Iranian government has used the U.S. product SmartFilter to block offensive websites, but the ONI reports that it now has a homegrown system for searching the Internet for objectionable content and keywords. This makes Iran and China the only two countries that "aggressively filter" Internet content using their own technology.
Faced with similar unrest, other governments have pulled the plug on Internet communications entirely. Iran's authorities appear to have chosen to begin "bandwidth throttling" instead. By limiting the amount of information that gets through every second, the government can effectively slow down the Internet so that the average Internet user has to wait several minutes to add a post to Twitter or upload an image to Flickr. With reduced bandwidth, Zuckerman says, "it's harder to access Internet content from the outside, and it's really hard to upload content."
Some analysts suggest it is unlikely that Iran's Internet connectivity would ever be turned off completely. "It's one thing to anger a group of protesting rioters," says Hal Roberts, also of Harvard's Berkman Center. "It's another to hurt the whole population" by shutting off Internet connection. With around 23 million Internet users in Iran, or about 35 percent of the population, Iran has far more Internet users than its Middle Eastern neighbors.
Andrew Lewman, a member of the team behind Tor--software that routes Internet traffic around government filters anonymously--says that he's surprised by how little the Iranian government has blocked the Internet in recent days, given the attention that the current political unrest has received. He attributes the continuing flow of information out of Iran to two possibilities: either there are people in the government who want to see it disseminated, or the government is tracking and recording everything that's happened in order to round up the perpetrators later. The government's main focus right now, Lewman says, is most likely dealing with the actual protestors on the streets.
Rob Faris, who contributed to the ONI report, is less optimistic about communication flow in Iran. The government has "ramped up filtering in a big way," he says. Even though Twitter remains accessible--through third party apps that don't access Twitter.com for example--"let's not kid ourselves," Faris says. "Access to Twitter, without all the other things you can do with the web, isn't a good deal." Meanwhile, the other measures Iran has taken have "significantly impacted" the communications infrastructure. "They've gone from a repressive regime to a more repressive regime," Faris says.
Still Roberts believes that the Iranian government will likely crack down on the rioters first, and deal with the bloggers later. He suggests that government agencies may be tracking users via their Internet protocol addresses and planning to follow up with arrests.
The most difficult question regarding the Web's involvement in the current situation, Zuckerman says, is to what extent these tools are helping to organize actual protests. "This is a legitimate street protest; people are extremely upset about their voting rights," he says. Zuckerman senses that the technology isn't helping opposition supporters as much as are traditional organizing methods like phone calls and word of mouth.
According to Stephen Murdoch, a computer security researcher at the University of Cambridge, it's hard to tell how many people are actually involved with Web-based protests inside Iran because what we see outside the country is a "biased" sample. Twitter and Facebook are popular in the United States, but there are likely other social-networking sites geared toward Iranians that we can't monitor as closely. So the extent--and reach--of Web activity in Iran is hard to judge.
But the effect on the global community is clear, Roberts says: "The press is driven by [Iran's] Twitter stream."
Copyright Technology Review 2009.
-----
fabric | rblg
This blog is the survey website of fabric | ch - studio for architecture, interaction and research.
We curate and reblog articles, researches, writings, exhibitions and projects that we notice and find interesting during our everyday practice and readings.
Most articles concern the intertwined fields of architecture, territory, art, interaction design, thinking and science. From time to time, we also publish documentation about our own work and research, immersed among these related resources and inspirations.
This website is used by fabric | ch as archive, references and resources. It is shared with all those interested in the same topics as we are, in the hope that they will also find valuable references and content in it.
